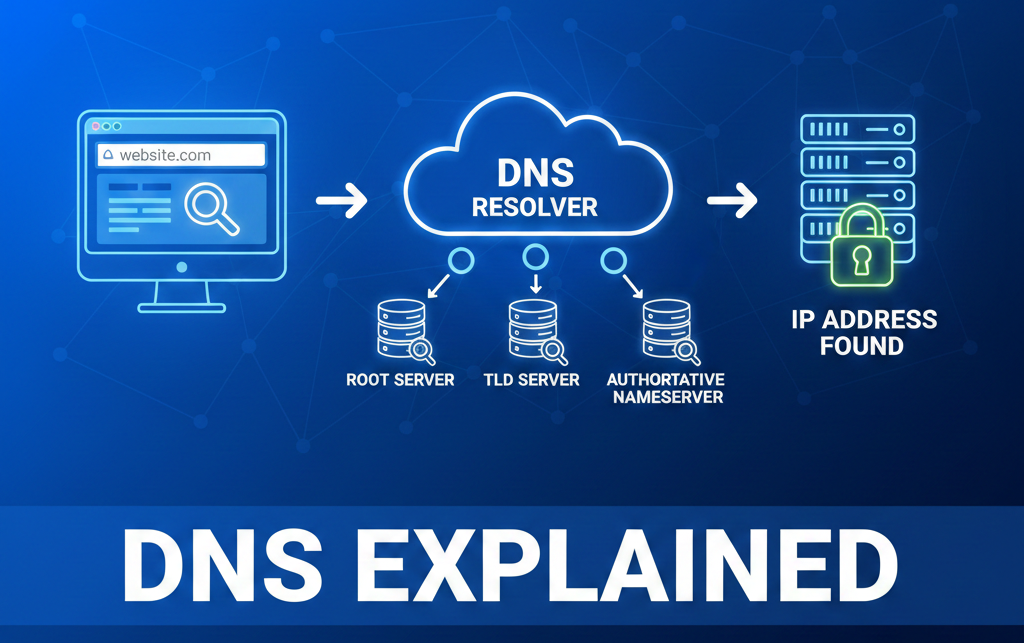
The internet relies on the Domain Name System (DNS) to translate human-friendly website names, like “example.com,” into numerical IP addresses that computers use to connect. DNS acts like the internet’s phonebook.
What is DNS Spoofing?
DNS spoofing (also called DNS cache poisoning) is a cyberattack where hackers trick a DNS server or your device into using fake information. Instead of directing you to the real website’s IP address, it sends you to a malicious one controlled by the attacker.
Imagine typing “bank.com” into your browser, expecting your bank’s site, but ending up on a fake page that looks identical to it. The attacker intercepts or forges the DNS response, replacing the legitimate IP with their own. This often exploits vulnerabilities in DNS protocols, such as a lack of response verification or predictable query IDs.
Common types include:
- Cache Poisoning: The attacker injects false data into a DNS server’s cache, affecting many users until the cache clears.
- Man-in-the-Middle (MITM): The hacker positions themselves between your device and the DNS server (e.g., on public Wi-Fi), intercepting queries and sending fake replies.
Why is DNS Spoofing Used?
Attackers use DNS spoofing mainly for malicious purposes:
- Phishing → Redirect users to fake sites to steal login credentials, credit card details, or personal information.
- Malware Distribution → Send victims to sites that automatically download viruses, ransomware, or spyware.
- Data Theft → In MITM scenarios, eavesdrop on unencrypted traffic or inject harmful content.
- Censorship or Disruption → Governments or entities block access to sites by redirecting to fake pages (e.g., China’s Great Firewall).
- Financial Gain → In cases like cryptocurrency attacks, steal funds by mimicking wallet services.
Real-world examples include the 2018 attack on MyEtherWallet, where DNS hijacking redirected users to a phishing site, resulting in the theft of crypto funds, and incidents targeting banks or public Wi-Fi to capture sensitive data.
Where is DNS Spoofing Used?
These attacks commonly occur in:
- Public Networks: Unsecured Wi-Fi in cafes, airports, or hotels, where MITM is easier.
- Compromised DNS Servers: ISPs or organizational resolvers poisoned to affect thousands.
- Local Devices: Malware altering your computer’s DNS settings.
- Global Scale: Nation-state operations for surveillance or censorship.
DNS spoofing remains a threat because many systems still lack complete protection like DNSSEC (which verifies responses digitally). To stay safe, use trusted DNS providers (e.g., Cloudflare or Google), enable HTTPS, and avoid unsecured networks.